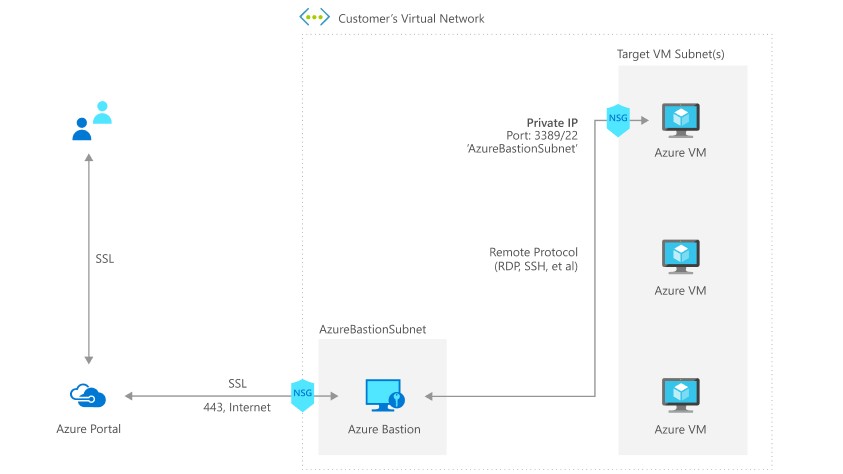
Microsoft Azure has recently launched Azure Bastion; a managed PaaS service to securely connect to Azure Virtual Machines (VMs) directly through the Azure Portal without any client needed.
Generally, we connect to the remote machines by either RDP or SSH. Before Bastion, if we need to connect to a VM in Azure we either need to expose a public RDP/SSH port of the server(s) or we need to provision a separate jump box server with said ports exposed and then connect to the private machines via the jump box server.
Exposing RDP/SSH ports over the Internet is not desirable and considered as a security threat, and with Azure Bastion, we can connect to Azure VM(s) securely over SSL, directly in Azure Portal and without exposing any ports. This also enables clientless connectivity meaning no client tool like mstsc is needed. It just requires a supported browser to access the VM.
Key points
- Azure Bastion is a fully managed PaaS service that provides secure and seamless RDP/SSH access to Azure VM(s)
- No RDP/SSH ports need to be exposed publicly
- No public IP is required for VM(s)
- Access VM(s) directly from the Azure portal over SSL
- Help to limit threats like port scanning and other malware
- Makes it easy to manage Network Security Groups (NSGs)
- It is basically a scale set under the hood, which can resize itself based on the number of connections to your network
- Azure Bastion is provisioned within a Virtual Network (VNet) within a separate subnet. The name of the subnet must be AzureBastionSubnet
- Once provisioned, access is there for all VMs in the VNet, across subnets
- Get started within minutes
Getting Started
- Select the VNet, in which you have the VM(s), which you want to connect. Create a subnet on which the bastion host will be deployed. Make sure that the range of networks is at least /27 or larger and the name of the subnet is AzureBastionSubnet.
- Now go to the Azure portal and create a Bastion service and fill in the required details.
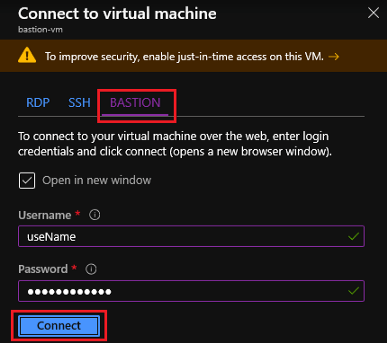
- Once the Bastion is provisioned, just navigate to the VM, you want to RDP/SSH and click Connect. There you will see an option to connect using Bastion.
- Just enter the username and password and Connect. You can also login using a username and SSH private key for Linux if it is configured.
- This is it. When connected, the remote session will start in the browser window.
Limitations
The service is not available in all regions, and the Azure folks are working on adding it to all regions eventually. As of now, the file transfer service is not available but we hope this feature will get added in the future, however, text copy-paste is supported. Keep visiting the service documentation for more details and feature updates.