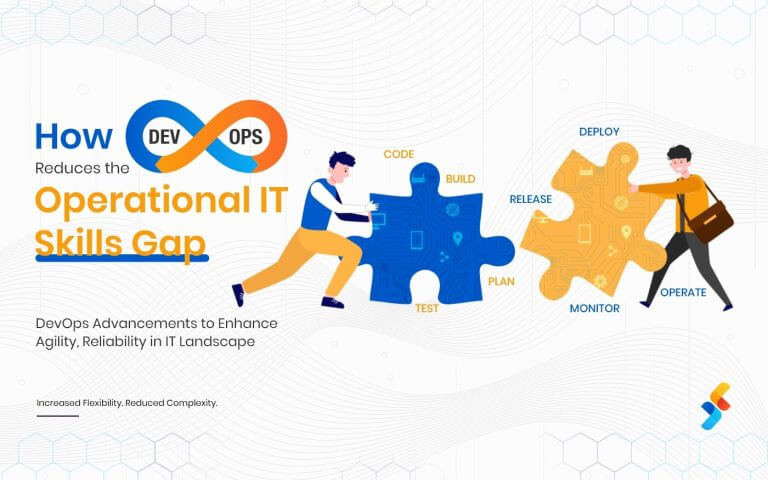
Unlock Infinite Possibilities For Your Digital Evolution With Cloud Consulting Services
Successive Digital is a pioneer in Cloud Consulting Services for all major Public Cloud providers, including AWS, Azure, and GCP. As a strategic partner, we provide exceptional insights and specialized solutions to help you maximize your cloud strategy. Our specialists facilitate a smooth transition from developing robust migration strategies to designing scalable cloud native solutions. Utilize the full potential of cloud technologies with our thorough assessments, cost-effective tactics, and ongoing support.
As a pioneer cloud consulting company, we help you drive to new heights in business with digital solutions supported by multi-cloud specialists who are dedicated to your success. At the crossroads of knowledge and technical skills, we create the way for your digital greatness in the cloud, allowing you to embrace a future where success is not just a goal but a continuous evolution.
Accelerate Intelligence And Value Across Business With Our Cloud Consulting Services
Transform your business with our cloud consulting services, designed for unparalleled efficiency. Our cloud specialists and solution architects tailor solutions to your needs, ensuring seamless data management and scalable infrastructure.

Cloud Migrations
Step into a seamless migration experience for your cloud journey with professional AWS cloud consulting services. Our certified AWS professionals provide personalized guidance on migrating to the cloud tailored to your business needs and ensure optimal usage of cloud resources.

Hybrid/Multi-Cloud
Our cloud consulting services comprise personalized hybrid and multi-cloud solutions. It aims to help you strategically and seamlessly integrate and manage multiple cloud platforms for better efficiency, scalability, agility, and operational excellence for both legacy applications and greenfield developments.

Backup & Disaster Recovery
Having expertise in AWS cloud consulting services, we help you with cloud only backup and disaster recovery planning and implementation strategies. Our assistance enables you to safeguard your unique data, maintain business continuity and ensure business resilience in any scenario.

Kubernetes Adoption
Get hands-on assistance with adopting Kubernetes, tailored to your application architecture, to enhance scalability and efficiency in containerized environments.

Container & Microservices
Our consultants work closely with you to design a personalized transition plan from monolithic to microservices architecture, ensuring a smooth and effective transformation.

CI/CD Consulting
Receive personalized consulting to streamline your development pipelines, incorporating CI/CD best practices for faster and more reliable software delivery.

SRE Consulting
Our Site Reliability Engineering experts offer personalized assessments and recommendations to enhance your system's reliability, minimizing downtime and optimizing performance.

Networking, Service Mesh
Benefit from personalized network architecture design and service mesh implementation, ensuring robust and secure communication tailored to your business needs.

DevSecOps Consulting
Our consultants provide personalized guidance to seamlessly integrate security into your development and operations processes, tailored to your unique business requirements.
Our Journey
10+
Years in Business100+
Clients served7
Worldwide OfficesExplore The Benefits Of Our Cloud Consulting Services

Strategic Cloud Planning
Unlock unparalleled business advantages through meticulous planning and strategy formulation. Our expert consulting team tailors solutions to your organization's unique needs, ensuring a strategic approach that aligns with your goals.
Efficient Migration Solutions
Being a leading cloud consulting company, we ensure a seamless transition to the cloud with migration planning and implementation strategies. We ensure you experience minimal disruption and maximum efficiency during migration.

Cost Optimization Strategies
Experience substantial cost savings with our innovative approaches to optimizing cloud resources. Our consulting-driven strategies guarantee that you get the most value for your investment, maximizing efficiency and minimizing expenses.

Robust Security Measures
Trust in our comprehensive security protocols designed to safeguard your digital assets. As a cloud consulting company, we prioritize robust security measures, providing a secure environment for your critical data through expert guidance and implementations.
Performance Enhancement
Elevate your digital capabilities with our performance optimization techniques. Our consulting-driven approach focuses on enhancing the speed and reliability of your cloud-based applications, ensuring optimal performance for your business processes.

24/7 Support and Monitoring
Rely on our dedicated consulting and support team for round-the-clock assistance and proactive monitoring. We ensure your cloud infrastructure operates at peak performance, offering continuous support to address any concerns and optimize your digital environment."
Success Stories
Logics LLC, USA
We have been continually working with technology experts at Successive. I appreciate them looking at our infrastructure to provide suggestions and I’m very impressed with their growth in recent years.
Ben Van Zutphen
Founder & CEO
CRE Models, USA
We worked on our first project 6 years ago, our business invests in real estate technology companies and we use their services for all the subsidiary companies that we invest in. I highly recommend them for any requirement you may have in the technical world.
Mike Harris
Managing Director
EWP, USA
When we first got in touch with Successive, we were looking to develop a sophisticated search technology integrated with an AI software system. It was a highly complex project that required a lot of adroitness which is exactly what Successive provided us with.
Myles Levin
President
PlayBetr, USA
We have been delighted working with Successive Digital. They helped us achieve and exceed our business goals. From Laravel, Json, Node to any technology or feature, the team delivered extreme standardization, excellence, and streamlined automation. Thumbs up to Sid and his team.
Marvin Jones
Director
Frontier Precision, USA
The process of Successive Digital is extremely smooth and commendable. I loved the upfront communication, well-organized sprints and immersive documentation, especially the Redmine system, to track daily progress easily. We are looking forward to working with Successive on our upcoming projects too.
Chad Minteer
CEO
Display Now, USA
I am extremely grateful to Successive Digital for being a wonderful and strategic partner. The team promptly understood the concept, took daily mockups, presented a comprehensive set of specifications, turned them into designs and built a scalable solution. It’s been awesome working with you guys
Chris Dukich
Founder
Discover the Potential of Cloud Consulting Services With Successive Digital
Ensure the maximum benefits of cloud technology in four ways and achieve your business goals.
Faster Development
We assist you in implementing effective DevOps processes such as continuous code integration, testing, and delivery. Our cloud consulting services include guiding you at every step and ensuring the growth of your organization.
Reliability
We guide you in developing fault-tolerant applications and infrastructure designs for your applications. As an experienced cloud consulting company, we leverage business acumen in different industries and cloud excellence to ensure high application reliability and rapid recovery.
Enhanced Security
We rely on our efficient and transparent information security management processes to assist you with encrypting data at rest and in transit, implementing granular access control, developing user behavior standards, conducting security training, and more.
Optimized Costs
We help you realize the end-to-end adoption of cloud solutions along with analyzing real-world benefits and cost savings in the long run.
Global Industry Evolution Through Innovation
We've earned expertise across various industries and offer our customers valuable insights and beneficial solutions.

Fintech
We transform the future of the banking, insurance, and finance sectors with innovation-intensive fintech application development.

Healthcare
We offer industry-leading digital health solutions enabling healthcare practitioners across multiple sectors, including hospitals, private clinics, and MedTech organizations.

AgriTech
We modernize the entire farming value chain and create effective systems and innovative tech-oriented business models to drive massive ROI in the agriculture space

Logistics & Distribution
Enhancing end-to-end user journey of supply chain and logistics with digital transformation and technology solutions, increasing application navigation, availability, and user experience.

Media & Communication
Developing intelligent and automated media and advertising platforms delivering hyper-personalized experiences and efficiency to achieve evolving business needs.